If you’re dealing with permission issues on your server and come across advice suggesting you use chmod 777 on your directory, it’s crucial to understand what this command does and why it’s generally unsafe.
Here’s a simplified explanation of Linux file permissions and why you should avoid using chmod 777.
We also created an infographic for your reference.
Table of Contents
What Are Linux File Permissions?
Imagine Linux file permissions as a security guard for your files and directories. They decide who can enter (read), modify (write), or use (execute) your files.
Get Your Free Linux training!
Join our free Linux training and discover the power of open-source technology. Enhance your skills and boost your career! Learn Linux for Free!
Understanding how these permissions work is key to keeping your system secure and ensuring that only the right people can access your data.
Every file or directory in Linux is managed with:
- An Owner: The person who created the file.
- A Group: A set of users who can share access to the file.
- Others: The permissions that apply to all other users.
There are three basic types of permissions:
- Read (r): Allows you to open and view the file or list the contents of a directory.
- Write (w): Lets you edit the file or change what’s inside a directory, like adding or deleting files.
- Execute (x): Enables you to run the file as a program or access the contents of a directory.
How to View File Permissions in Linux
You can see a file’s permissions using the ls -l command. For example:
ls -l filename.txtThis might show output like:
-rw-r--r-- 12 howtouselinux users 12.0K Apr 8 20:51 filename.txt
Here’s what it means:
- -rw-r–r–: This indicates the permissions.
- –: Regular file
- rw-: Owner can read and write
- r–: Group members can read
- r–: Others can read
Numeric Permission Codes
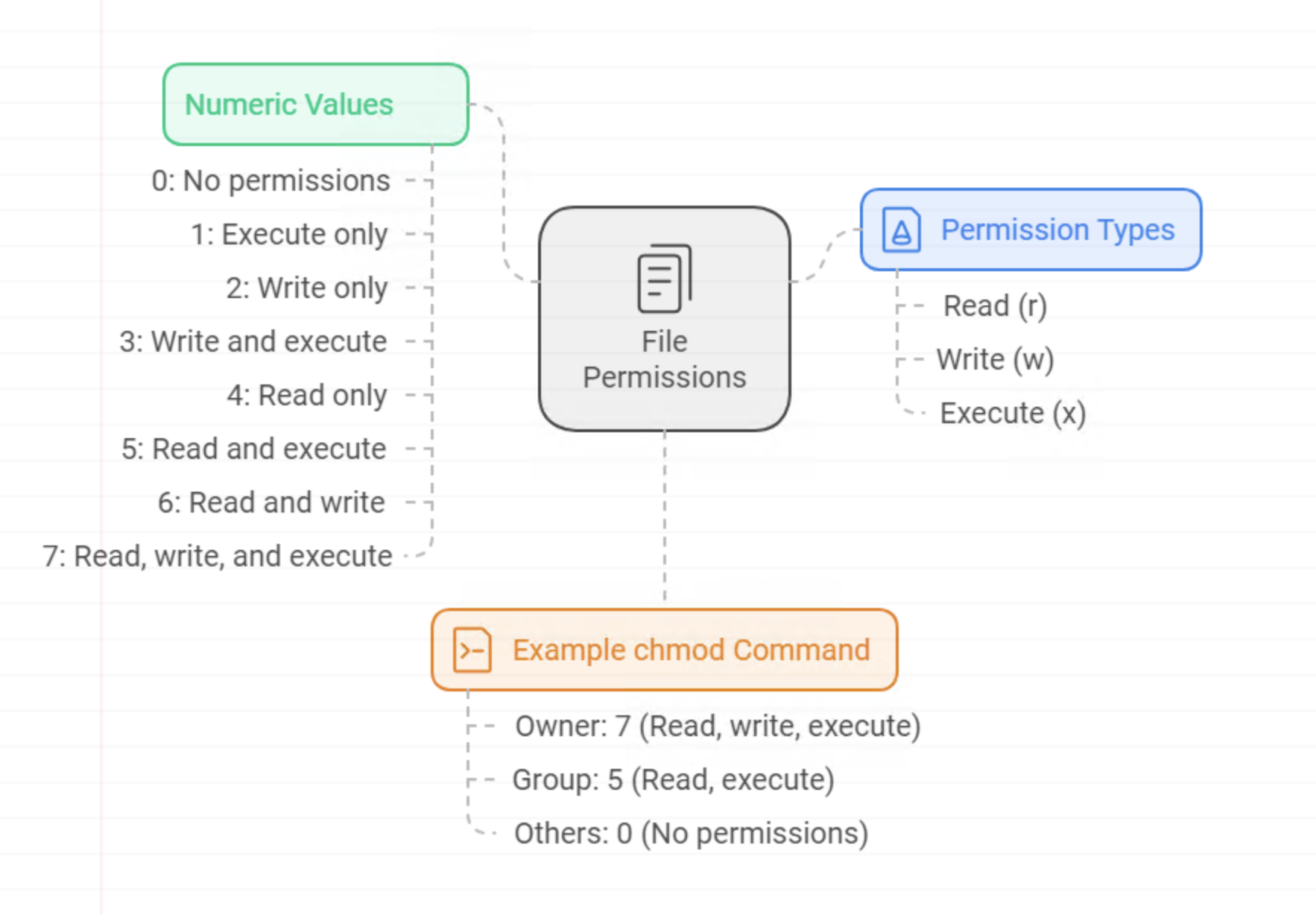
Permissions can be expressed numerically. Each permission type has a specific value:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
You add these values to set the desired permissions:
- 0: No permissions
- 1: Execute only
- 2: Write only
- 3: Write and execute
- 4: Read only
- 5: Read and execute
- 6: Read and write
- 7: Read, write, and execute
For example, chmod 750 means:
- 7 (Owner): Read, write, and execute
- 5 (Group): Read and execute
- 0 (Others): No permissions
Why chmod 777 is Dangerous

Setting permissions to 777 gives read, write, and execute access to everyone on the system. This is risky because:
- Any user can read, modify, or delete the file.
- Potentially malicious users could exploit this to compromise your system.
If you face permission problems with your server, avoid 777. Instead:
- Change file ownership to the user running the application using chown.
- Set appropriate permissions:
- Directories: chmod 755
- Files: chmod 644
Here’s how you might do it for a directory:
chown -R howtouselinux:howtouselinux /var/www
find /var/www -type d -exec chmod 755 {} \;
find /var/www -type f -exec chmod 644 {} \;Only root or users with sudo privileges can change permissions, so be cautious when using chmod.
File permission Infographic
Introduction to File Permissions
File permissions determine who can read, write, or execute a file. Permissions are denoted by a combination of characters or numbers.
Understanding Permission Notation
Permissions are displayed in a 10-character string. For example:
-rwxr-xr--| Character | Description |
|---|---|
| – | File type (e.g., ‘-‘ for regular file, ‘d’ for directory) |
| r | Read permission |
| w | Write permission |
| x | Execute permission |
File Permission Categories
Permissions are categorized into three types: User (u), Group (g), and Others (o). Each type can have read (r), write (w), and execute (x) permissions.
| Category | Read (r) | Write (w) | Execute (x) |
|---|---|---|---|
| User (u) | ✓ | ✓ | ✓ |
| Group (g) | ✓ | ✓ | ✓ |
| Others (o) | ✓ | ✓ | ✓ |
Numeric Permission Codes
Numeric permission codes represent permissions using octal (base-8) numbers. Each digit in the numeric code represents a set of permissions for user, group, or others.
The numeric code consists of three digits, where each digit is a sum of permissions:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
The sum of these values determines the permissions:
- 7 = 4 (read) + 2 (write) + 1 (execute)
- 6 = 4 (read) + 2 (write)
- 5 = 4 (read) + 1 (execute)
- 4 = 4 (read)
| Numeric Code | Permissions | Description |
|---|---|---|
777 |
rwxrwxrwx | All permissions granted |
755 |
rwxr-xr-x | Owner has full permissions; others can read and execute |
644 |
rw-r–r– | Owner can read and write; others can read |
Changing File Permissions
To change file permissions, use the
chmod command in the terminal.You can use either symbolic notation (e.g.,
chmod u+x file.txt) or numeric notation (e.g., chmod 755 file.txt).Conclusion
Understanding file permissions is crucial for managing security and access control in your system.
Always review permissions carefully, especially when sharing files or folders.

Conclusion
Understanding Linux file permissions is essential for managing your system securely.
Avoid using 777 permissions as it exposes your files to unnecessary risk. Stick to safer permission settings and adjust ownership as needed for proper access control.
Feel free to ask any questions or leave comments if you need further clarification!

Edward Dan
Saturday 14th of September 2024
Great. The infographic is amazing.