Ever wondered if a remote port is open or closed on a remote Linux system? Linux provides us with a straightforward solution right at our fingertips: shell commands. In this article, we’ll explore a simple yet effective method to test the status of a remote port using shell commands. Prerequisites: Before proceeding, ensure that you …
The idea of artificial intelligence (AI) freaks some people out because they’re worried it might take their jobs. But hey, AI can actually be a huge helper in all kinds of work, from writing and designing to marketing and teaching. It’s already proven itself to be super useful, and for some tasks, we just can’t …
Efficient management of Kubernetes clusters is paramount to ensuring the reliability, security, and optimal performance of your containerized applications. Here are four comprehensive strategies to enhance your Kubernetes management skills: Implement Automated Monitoring and Alerts Importance: Continuous monitoring is vital for maintaining the health of your Kubernetes ecosystem, allowing for early detection and mitigation of …
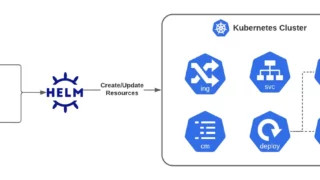
As a seasoned Linux administrator, you’re well-versed with the convenience and efficiency brought by package managers like apt, yum, or zypper. These tools have been indispensable in managing software packages, handling dependencies, and streamlining installations and updates on Linux systems. Transitioning into the Kubernetes ecosystem, you’ll find a parallel tool that brings similar benefits to …
Kubernetes, the container orchestration platform, has revolutionized how applications are deployed and managed. But running Kubernetes effectively requires a reliable cloud infrastructure. With numerous cloud providers offering Kubernetes solutions, choosing the right one can be overwhelming. This article outlines a framework to help you navigate this decision-making process. We’ll explore key factors to consider beyond …
Securing a position as a DevOps Engineer is a competitive process that requires showcasing both your technical expertise and alignment with the collaborative, agile principles that underpin the DevOps culture. To help you stand out in your interview, here are detailed tips and strategies: Showcase Collaboration Skills DevOps thrives on seamless collaboration between development, operations, …
Kubernetes is a powerful container orchestration tool, but it can also be complex, leading to common points of confusion among its users, especially when it comes to understanding pods. Here are some aspects of Kubernetes pods that users often find confusing: Pods vs. Containers Confusion: Many new Kubernetes users conflate pods and containers, thinking they …
To check the status of a container within a Kubernetes environment, you can use the kubectl command-line tool, which is the standard way to interact with your Kubernetes cluster. Below are the steps to check the status of a container: List Pods First, list all the running Pods in your Kubernetes cluster to identify which …
On February 19, local time, the European Commission initiated a formal investigation into TikTok. This inquiry aims to assess whether TikTok’s practices in areas such as minor protection, algorithmic design for addiction, advertising transparency, and data access for researchers comply with the stipulations of the Digital Services Act. TikTok, with over 1 billion monthly active …
NVIDIA announced its fourth-quarter and fiscal year earnings ending January 28, 2024. Fourth-quarter revenue was $22.1 billion, compared to $6.051 billion in the same period last year, representing a 265% year-over-year increase and a 22% sequential increase. Data center revenue for the quarter was $18.4 billion, a 409% increase year-over-year and a 27% increase sequentially. …