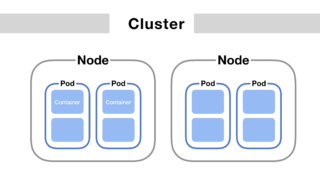
To list all the containers running in a Kubernetes cluster, you would typically start by listing all Pods, as containers are encapsulated within Pods in Kubernetes. Each Pod can run one or more containers. Here’s how you can list all containers across all namespaces in a Kubernetes cluster: Using kubectl to list all the containers …
Kubernetes, or K8s, stands as a pivotal force in the contemporary landscape of container orchestration, offering a robust platform for deploying, scaling, and managing containerized applications. A critical aspect of Kubernetes’ functionality revolves around resource management, particularly in terms of CPU and memory allocations for the containers within pods. Understanding how Kubernetes interprets and utilizes …
Identifying the busiest pod in a Kubernetes cluster, in terms of resource usage (CPU and memory), involves a few steps. There isn’t a direct kubectl command that gives you this information outright, but you can use a combination of commands and tools available in Kubernetes to get the insights you need. Here’s how you can …
In Kubernetes, when configuring a Service to expose your applications, you’ll encounter three key port concepts: port, targetPort, and NodePort. Understanding the distinctions and relationships between these ports is crucial for effectively managing access to your applications running within Pods. port Definition: The port field in a Service specification defines the port on which the …
In Kubernetes, when defining a Service to expose your application, the concept of targetPort plays a crucial role in routing incoming traffic to the correct destination within your Pods. What is targetPort? Definition: targetPort is a field in the Service definition that specifies the port on the Pod containers to which the traffic should be …
Minikube is a tool that simplifies the process of running Kubernetes locally, making it easier for developers to develop and test Kubernetes applications. One of the key concepts in Minikube is the use of “drivers” to set up and manage the Kubernetes cluster’s virtual environment. Understanding Minikube drivers is crucial for configuring Minikube to suit …
In a Kubernetes environment, understanding the different types of IP addresses and how they are used is crucial for managing communication within and outside the cluster. understanding different types of IP addresses in Kubernetes To illustrate these concepts, let’s consider a scenario with a Kubernetes cluster consisting of 3 nodes, 3 Pods, each part of …
Kubernetes, the orchestration system for managing containerized applications, offers a variety of service types to ensure your applications are accessible and communicate efficiently. Each service type caters to specific use cases, balancing accessibility with resource allocation. Let’s delve into the primary Kubernetes Service types—ClusterIP, NodePort, LoadBalancer, and cloud provider-specific LoadBalancers—to understand their use cases and …
Pods are foundational to building and running applications in Kubernetes. They provide the execution environment for containers, encapsulating application components, managing their lifecycle, and facilitating inter-component communication and resource sharing. A Pod encapsulates one or more containers, storage resources, a unique network IP, and options that govern how the container(s) should run. Containers within a …
minikube start –vm-driver=none 😄 minikube v1.32.0 on Ubuntu 20.04 ✨ Using the none driver based on existing profile 👍 Starting control plane node minikube in cluster minikube 🔄 Restarting existing none bare metal machine for “minikube” … 🔗 Exiting due to NOT_FOUND_CNI_PLUGINS: 💡 Suggestion: The none driver with Kubernetes v1.24+ requires containernetworking-plugins. Exiting due to …