“Practical Linux System Administration” by Kenneth emerges as a remarkably comprehensive guide for anyone aspiring to master the intricacies of Linux administration. This book is a treasure trove of practical knowledge, seamlessly blending fundamental concepts with advanced techniques. From the outset, Kenneth’s expertise shines through. He meticulously introduces the Linux operating system, making it approachable …
David Cao
The noexec option in /etc/fstab (File System Table) in Linux is a mount option that specifies how a filesystem should be mounted, particularly with regard to the execution of binaries. When a partition is mounted with the noexec option, it means that you cannot execute any binaries that are stored on that partition. Understanding /etc/fstab …
To fix the “no matching host key type found” error in SSH, you need to modify your SSH client configuration to accept the host key types offered by the SSH server. This error typically occurs when your SSH client does not support or is not configured to accept the host key types provided by the …
In today’s data-driven environment, Excel’s XLOOKUP function is a game-changer, particularly for performing lookups across different worksheets and even different workbooks. This versatility allows for more integrated and complex data analysis. Let’s dive into how you can effectively use XLOOKUP for cross-worksheet and cross-workbook lookups. Understanding XLOOKUP for Cross-Worksheet Lookups Cross-worksheet lookups are essential when …
The search_mode parameter in the XLOOKUP function in Microsoft Excel specifies the direction or method Excel should use when searching for the lookup_value. This parameter can greatly affect how the function operates, especially in large datasets or specific search scenarios. Here’s a detailed explanation of each option within the search_mode parameter, along with examples. Introduction …
The XLOOKUP function in Excel is powerful, but like any tool, it can occasionally yield errors. Understanding these common issues and knowing how to resolve them is crucial for efficient use of XLOOKUP. Here are some of the frequent errors encountered with XLOOKUP and strategies to fix them: 1. #N/A Error: Value Not Found Cause: …
In the world of Linux and Unix-like operating systems, the “Permission Denied” error is a common occurrence that stumps many users, particularly when encountered in situations where file permissions seem to be correctly set. One less obvious but significant cause of this error is the `noexec` mount option. Understanding how this option works is key …
Migrating a WordPress website can be a daunting task, especially when you’re looking for a hosting service that can handle your growing needs. Several challenges can arise during WordPress migration. One common issue is the potential for data loss, especially with sites that have extensive content or complex structures. Ensuring complete and accurate backups before …
Welcome to my Cloudways hosting review. It’s been well over a year since I made the switch to Cloudways hosting. Hosting is a very important “blogging tool“. After all, it’s the engine that drives websites. Don’t settle for garbage because it can make a difference. When searching for the best web hosting service, it’s crucial …
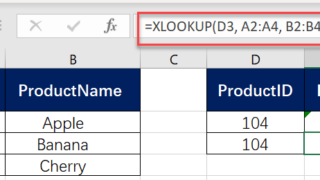
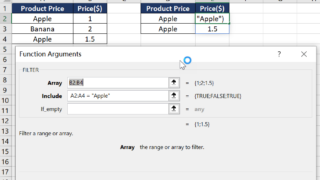
While XLOOKUP in Excel is primarily designed to return the first match, it can be combined with other functions like FILTER or TEXTJOIN, or used with an array formula to return all matches for a given criterion. XLOOKUP Returns the First Match in Excel This is an example to demonstrate how XLOOKUP in Excel is …