Ever encountered the cryptic message “Remote Host Key Has Changed” while connecting to a server using SSH (Secure Shell)? This seemingly technical error notification actually serves as a vital security safeguard. Each server in the SSH world has a one-of-a-kind identifier called a host key, similar to a digital fingerprint. When you connect for the …
David Cao
In Linux, getting the SSH host key fingerprint is crucial for verifying the identity of an SSH server before establishing a connection. Here are the methods to retrieve the host fingerprint: Method 1: Using ssh-keygen Local Server: To find the fingerprint of a local SSH server’s host key, use: ssh-keygen -lf /etc/ssh/ssh_host_rsa_key.pub The -l option …
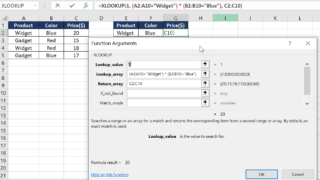
Utilizing XLOOKUP with multiple criteria in Excel allows for more flexible data searching compared to traditional lookup functions. This capability enhances data analysis by enabling searches based on several conditions. Method 1: Using Boolean Logic in XLOOKUP Combine multiple criteria using Boolean (AND) logic within the XLOOKUP function: XLOOKUP(1, (CriteriaRange1=Criteria1) * (CriteriaRange2=Criteria2) * …, ReturnRange) …
When connecting to an SSH server, especially for the first time, users often encounter a security prompt. This prompt plays a crucial role in the SSH connection process, ensuring the security and authenticity of the server being connected to. The authenticity of host ‘howtouselinux (10.254.175.51)’ can’t be established. ECDSA key fingerprint is SHA256:PgyFiC7Su7BiFBO1Sn8493MMz8/PE+2fJMI/mFfBy9M. Are you …
The error message bash: TMOUT: readonly variable indicates that the TMOUT variable has been set as readonly, which prevents you from changing its value in your current session. This is usually done for security reasons, often in a global configuration file, to enforce automatic logouts for idle sessions. To fix this and change the TMOUT …
Addressing SSH auto-logout issues often involves configuring two key settings: the TMOUT shell variable and the StopIdleSessionSec setting in /etc/systemd/logind.conf. Each plays a distinct role in session management and inactivity handling. TMOUT Variable: A Bash shell setting that defines the maximum idle time before automatic logout. It is crucial for users experiencing undesired SSH disconnections …
The XLOOKUP function in Excel includes an argument for “match mode,” which is crucial for determining how the function matches the lookup value with values in the lookup array. XLOOKUP(lookup_value, lookup_array, return_array, [if_not_found], [match_mode],[search_mode]) This affects how the function searches for and identifies the value being sought. Below is a breakdown of the different match …
Excel is one of the most popular spreadsheet software used by millions of people worldwide. It offers a wide range of functions and features that help people in data analysis, manipulation, and management. One of the powerful features of Excel is the XLOOKUP function which allows users to look up a specific value in a …
In today’s digital age, it is becoming increasingly important to sign electronic documents using electronic signatures instead of traditional handwritten signatures on paper. One challenge that arises is how to convert a paper-based signature into a transparent electronic signature within a Word document. In this article, we will explore how to achieve this and provide …
As an Excel user, you have likely encountered the problem of having unwanted spaces within your cell contents. Whether it’s due to importing data from another source, copy-pasting, or simply typing too quickly, it’s important to know how to swiftly remove those blank spaces to avoid errors in your work. In this article, we will …