The cloud computing landscape is booming, and with it comes a surging demand for skilled cloud security professionals. As an AWS expert interviewer, I’ve compiled a list of the top seven AWS security questions that I consistently ask candidates to assess their expertise in cloud security. These questions cover essential concepts and practices that are …
Cloud
Understanding the SSH Command for GitHub The command ssh -T -p 443 [email protected] is used to establish an SSH (Secure Shell) connection to GitHub’s Git services over the SSH protocol. Let’s break down the components of this command: ssh: This is the SSH client command used to connect to remote servers. -T: This option tells …
How to Prevent the Installation of Malicious Packages on Linux To safeguard your Linux system from the installation of malicious software packages, adhere to the following security measures: Use Official Repositories Always prefer packages from the official repositories of your Linux distribution, as they are maintained and regularly updated by trusted sources. Verify the authenticity …
SSH, or Secure Shell, is a critical tool for system administrators and developers for secure remote management of servers. In this article, we’ll explore some of the most common SSH problems, analyze their causes, and provide detailed solutions to get you back online quickly. SSH Connection Timeouts Issue: Users experience timeouts when trying to connect …
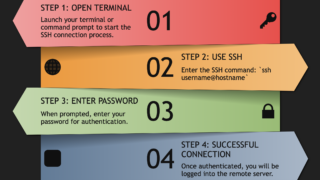
SSH, or Secure Shell, is a cryptographic network protocol that provides a secure channel for data exchange between a client and a server. It is widely used for remote login and other secure network services. In this comprehensive guide, we will delve into the fundamentals of SSH, explore its configuration and advanced techniques, discuss security …
Understanding GPG Signature Verification Error The error “GPG signature verification error: Bad GPG signature” typically occurs during package installation or repository metadata retrieval in systems like Red Hat Enterprise Linux (RHEL) or CentOS when the GPG signature of a package or repository metadata fails to verify successfully. GPG signature verification error: This indicates that the …
Portmapper, also known as rpcbind, serves as a mapping service for Remote Procedure Call (RPC) programs. It acts as a mediator between clients and RPC services, enabling them to locate and connect to each other efficiently. Portmapper maintains a registry of available RPC services and the ports they are listening on, facilitating dynamic assignment of …
6 powerful Linux commands to solve your network issues in minutes
As the sun sets on CentOS Linux with its End-of-Life (EOL) approaching on June 30th, 2024, many businesses and tech professionals are deliberating their next steps. In a recent online discussion, users shared their insights and experiences, shedding light on potential operating system replacements for CentOS. AlmaLinux Emerges as a Strong Contender AlmaLinux seems to …
The systemctl command is a powerful tool in Linux systems that serves as the interface to control and manage the systemd init system. It is a central component responsible for initializing, managing, and maintaining various system processes and services during the boot process and while the system is running. With systemctl, users can start, stop, …