The HostnameMismatchError is an exception that occurs in Python when there is a mismatch between the hostname specified in the URL you are trying to access and the hostname provided by the SSL certificate of the server you are connecting to. This error is typically raised by the requests library or when using ssl.wrap_socket with …
DevOps
Introduction Imagine your computer as a castle, and SSH as the special key to enter it safely. But just like in any adventure, there are secrets to making your castle extra secure. So get ready to explore, because we’re about to reveal some tricks that will make your castle unbreakable! Change the Default SSH Port …
SSH, or Secure Shell, is a cryptographic network protocol that provides a secure channel for data exchange between a client and a server. It is widely used for remote login and other secure network services. In this comprehensive guide, we will delve into the fundamentals of SSH, explore its configuration and advanced techniques, discuss security …
Understanding GPG Signature Verification Error The error “GPG signature verification error: Bad GPG signature” typically occurs during package installation or repository metadata retrieval in systems like Red Hat Enterprise Linux (RHEL) or CentOS when the GPG signature of a package or repository metadata fails to verify successfully. GPG signature verification error: This indicates that the …
Portmapper, also known as rpcbind, serves as a mapping service for Remote Procedure Call (RPC) programs. It acts as a mediator between clients and RPC services, enabling them to locate and connect to each other efficiently. Portmapper maintains a registry of available RPC services and the ports they are listening on, facilitating dynamic assignment of …
Overview In this tutorial, we’ll see the different ways in which we can combine and execute multiple Linux commands efficiently. We’ll be using Bash for our examples, so there could be slight differences with other shells. Why Combine Multiple Commands? Executing commands one after the other in a command line is a regular activity for …
Overview Linux is quite a robust operating system and, as such, Linux servers rarely need to be rebooted. However, sometimes there are reasons we do need to reboot our system. For example, if we’re running Linux on our personal computer, rebooting and shutting down the system could be everyday operations. In this tutorial, we’ll learn …
Efficient management of Kubernetes clusters is paramount to ensuring the reliability, security, and optimal performance of your containerized applications. Here are four comprehensive strategies to enhance your Kubernetes management skills: Implement Automated Monitoring and Alerts Importance: Continuous monitoring is vital for maintaining the health of your Kubernetes ecosystem, allowing for early detection and mitigation of …
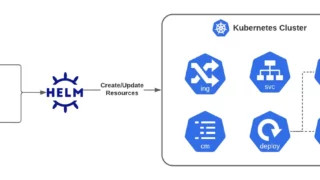
As a seasoned Linux administrator, you’re well-versed with the convenience and efficiency brought by package managers like apt, yum, or zypper. These tools have been indispensable in managing software packages, handling dependencies, and streamlining installations and updates on Linux systems. Transitioning into the Kubernetes ecosystem, you’ll find a parallel tool that brings similar benefits to …
Kubernetes, the container orchestration platform, has revolutionized how applications are deployed and managed. But running Kubernetes effectively requires a reliable cloud infrastructure. With numerous cloud providers offering Kubernetes solutions, choosing the right one can be overwhelming. This article outlines a framework to help you navigate this decision-making process. We’ll explore key factors to consider beyond …