Kubernetes, the orchestration system for managing containerized applications, offers a variety of service types to ensure your applications are accessible and communicate efficiently. Each service type caters to specific use cases, balancing accessibility with resource allocation. Let’s delve into the primary Kubernetes Service types—ClusterIP, NodePort, LoadBalancer, and cloud provider-specific LoadBalancers—to understand their use cases and …
DevOps
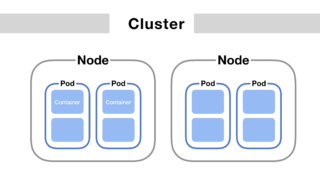
Pods are foundational to building and running applications in Kubernetes. They provide the execution environment for containers, encapsulating application components, managing their lifecycle, and facilitating inter-component communication and resource sharing. A Pod encapsulates one or more containers, storage resources, a unique network IP, and options that govern how the container(s) should run. Containers within a …
minikube start –vm-driver=none 😄 minikube v1.32.0 on Ubuntu 20.04 ✨ Using the none driver based on existing profile 👍 Starting control plane node minikube in cluster minikube 🔄 Restarting existing none bare metal machine for “minikube” … 🔗 Exiting due to NOT_FOUND_CNI_PLUGINS: 💡 Suggestion: The none driver with Kubernetes v1.24+ requires containernetworking-plugins. Exiting due to …
Minikube is an invaluable tool for developers looking to test and develop Kubernetes applications locally. However, when running Minikube with Kubernetes version 1.24 or higher using the none driver and Docker as the container runtime, you might encounter the NOT_FOUND_CRI_DOCKERD error. minikube start –vm-driver=none 😄 minikube v1.32.0 on AlmaLinux 8.6 ✨ Using the none driver …
minikube start –vm-driver=none 😄 minikube v1.17.1 on Ubuntu 20.04 ✨ Using the none driver based on user configuration ❌ Exiting due to GUEST_MISSING_CONNTRACK: Sorry, Kubernetes 1.20.2 requires conntrack to be installed in root’s path Understanding GUEST_MISSING_CONNTRACK error The error message you’re encountering indicates that conntrack, a required dependency for Kubernetes 1.20.2, is missing from the …
minikube start –vm-driver=none 😄 minikube v1.32.0 on Almalinux 8.6 ✨ Using the none driver based on user configuration ❌ Exiting due to GUEST_MISSING_CONNTRACK: Sorry, Kubernetes 1.28.3 requires crictl to be installed in root’s path The message you’re seeing is from attempting to start Minikube with a specific configuration on your Almalinux 8.6 system. Here’s a …
Using kubectl command to find the ip address of Pod in Kubernetes cluster To retrieve the IP address of a Pod in Kubernetes, you can use the kubectl command-line tool. Here’s how you can do it: List all Pods: First, if you need to find the specific name of the Pod whose IP address you …
Kubernetes Pod: Everything You Need to Know What is a Pod in Kubernetes? A Pod is the smallest, most basic deployable object in Kubernetes that represents a single instance of a running process in your cluster. Pods can contain one or more containers that share storage, network, and other resources. How do I list all …
To check the memory usage of a pod in Kubernetes, we have multiple methods: Using Direct Commands on Pods to get the memory usage in Kubernetes This method doesn’t require any third-party tools. Start by listing all the pods in your cluster with kubectl get pods Then, access the shell of the pod you’re interested …
Installing Stable Diffusion on a Mac, particularly those with Apple Silicon M1/M2 chips, offers several user-friendly options. Ways to Install Stable Diffusion on Apple Mac Using AUTOMATIC1111: This is a more technical route that involves cloning the web UI repository, placing Stable Diffusion models in the specified directory, and running commands in the terminal to …