What is SSH key? How do I use the SSH key in Linux? These are some of the most common questions that people have when it comes to ssh keys.
In this blog post, we will answer these questions and provide examples of how ssh keys work. We will also discuss the benefits of using ssh keys and how they can improve your security.
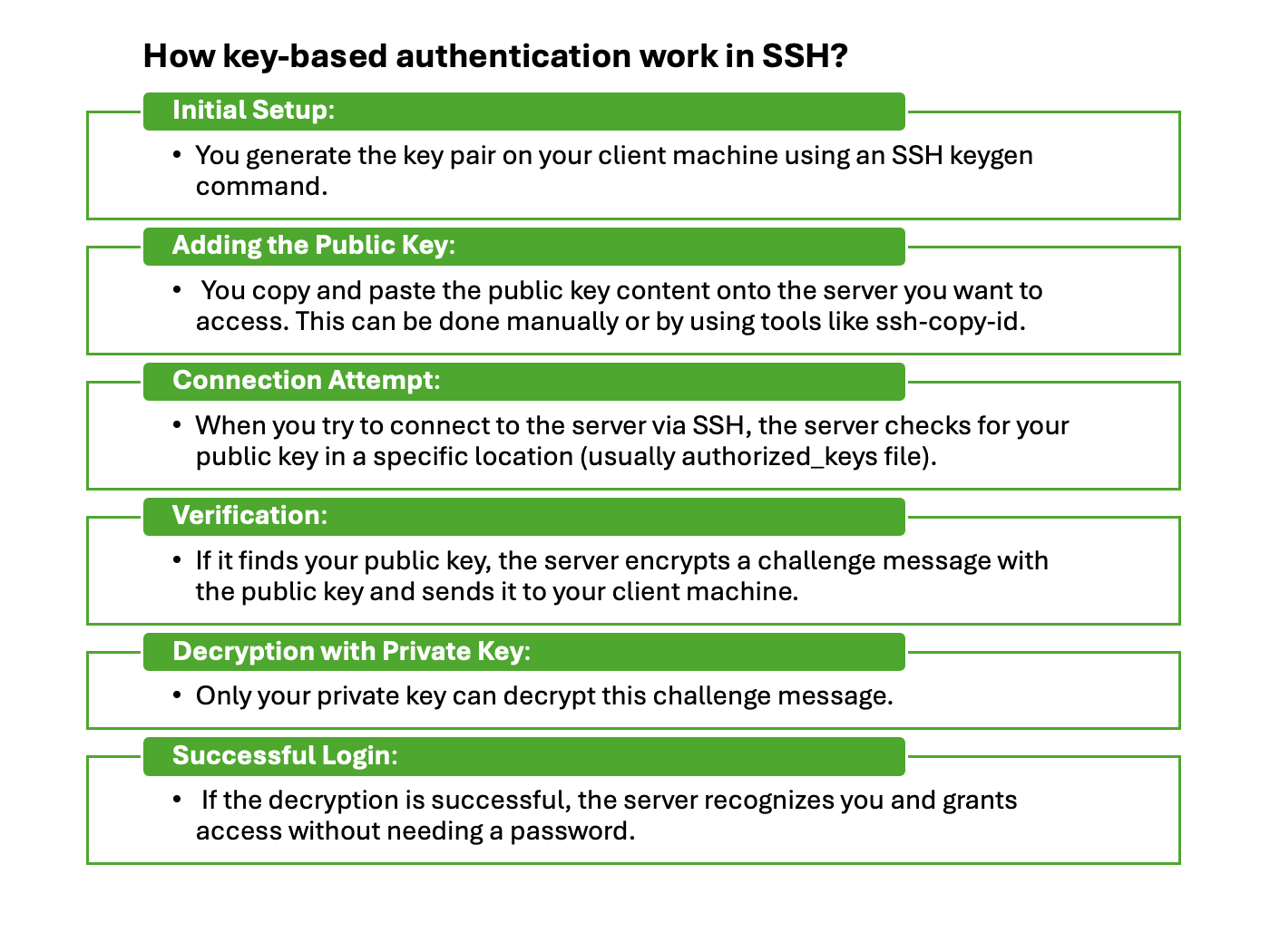
Table of Contents
What is SSH Key?
SSH key is based on public key infrastructure (PKI) technology. It is the gold standard for digital identity authentication and encryption. SSH keys are a pair of public and private keys.
Get Your Linux Course!
Join our Linux Course and discover the power of open-source technology. Enhance your skills and boost your career! Start learning Linux today for only $1!These keys not only improve security, but also enable the automation of connected processes, single sign-on (SSO), and identity etc. They are widely used in the Secure Shell (SSH) protocol.
What is key-based authentication in SSH?
The key-based authentication in SSH is a method of logging into a Linux or Windows system using a public and private key pair. The public key can be shared to the public, and the private key is stored in a local system.
- The private key is a secret file that should be kept on the client machine (your computer) and never shared with anyone.
- The public key is a different file that can be freely distributed, including being added to the server you want to connect to.
How key-based authentication works in SSH?
- Initial Setup: You generate the key pair on your client machine using an SSH keygen command.
- Adding the Public Key: You copy and paste the public key content onto the server you want to access. This can be done manually or by using tools like ssh-copy-id.
- Connection Attempt: When you try to connect to the server via SSH, the server checks for your public key in a specific location (usually authorized_keys file).
- Verification: If it finds your public key, the server encrypts a challenge message with the public key and sends it to your client machine.
- Decryption with Private Key: Only your private key can decrypt this challenge message.
- Successful Login: If the decryption is successful, the server recognizes you and grants access without needing a password.
How does ssh key encryption work?
The server uses the public key to encrypt a message and send it to the client. If the client has the correct private key, they can decrypt the message and send it back to the server for verification.
We can use command ssh-keygen to generate key pairs.
What are the benefits of using ssh key authentication?
The key-based authentication is more secure than password authentication. It is also more convenient than password authentication. You can add your public key to the authorized_keys file so that you can log in to your account without entering your password.
This makes it easier to log in to your account. If you lose your private key, you can use the ssh-keygen command to generate a new key pair.
- Easy and non-interactive login. Users don’t have to type the password for every new session
- More secure compared to passwords as it works on public-private key cryptography
- More reliable
- Better authentication and authorization management
- A good solution for both small and large infrastructure
- Easy to build and maintain
Which SSH Key type is safe?
SSH protocol supports several public key types for authentication keys. The key type and key size both matter for security. Based on the difference of each SSH key type, we recommend the following ways to generate SSH key file.
- ssh-keygen -t rsa -b 4096
- ssh-keygen -t dsa
- ssh-keygen -t ecdsa -b 521
- ssh-keygen -t ed25519
How to create an ssh key pair?
The first step is to create a key pair. To do this, open a terminal and run the following command:
ssh-keygen -t rsa -m pem
This will generate two keys, a public key and a private key. These two files will be stored in the ~/.ssh/ directory. You can change the location of these files by specifying a different path when you run the ssh-keygen command with -f option.
How to add public key to the authorized_keys file?
The authorized_keys file is located in the ~/.ssh/ directory, and it contains a list of all the public keys. To add your public key on the server side, run the following command:
ssh-copy-id -i ~/.ssh/id_rsa.pub user@board_ip
What if I lose my private key?
If you lose your private key, you can use the ssh-keygen command to generate a new key pair. ssh-keygen -t rsa -f ~/.ssh/id_rsa -C “your email address”
Can I use a password with ssh key authentication?
We can setup ssh with both public key and password. Login to the ssh server and edit the /etc/ssh/sshd_config file. Add the following line in the file: AuthenticationMethods “publickey,password”
How to login Linux with SSH key?
We can add the -i flag to specify the private key file in ssh command. For example, we can run the following command to login a remote host ([email protected]) with the private key host_key in the ~/.ssh/ directory.
ssh -i ~/.ssh/host_key [email protected]
We can also setup this up from SSH configuration file in client side. The SSH configuration file is a text file containing keywords and arguments. We can create a ~/.ssh/config file and add the Host & IdentityFile keywords there. Here is one example for this.
Host www.howtouselinux.com
IdentityFile ~/.ssh/host_key
What is the known_hosts File for ssh key in Linux?
Whenever we connect to a server via SSH, that server’s public key is stored in our home directory. The file is called known_hosts. When we reconnect to the same server, the SSH connection will verify the current public key matches the one we have saved in our known_hosts file. If the server’s key has changed since the last time we connected to it, we will receive a host key verification failed error (or one similar to it).
