In Linux, file permissions are an important part of keeping your system secure.
In this blog post, we will discuss two ways to check file permissions in Linux- using the “ls” command and using the “stat” command.
- The “ls” command is one of the most commonly used commands in Linux to list directory contents. By running “ls -l” in the terminal, you can view detailed information about files, including their permissions, ownership, size, and modification timestamps etc.
- The “stat” command provides more detailed information about a file, including file permissions in both numeric and symbolic formats. Running “stat” on a file will display various attributes, such as inode, size, access time, modification time, and more.
we will also discuss what each of the permissions means, and how to change them if necessary.
Get Your Linux Course!
Join our Linux Course and discover the power of open-source technology. Enhance your skills and boost your career! Start learning Linux today for only $1!Introducing the File Permission Calculator from How to Use Linux, a powerful tool designed to simplify the complex world of Linux file permissions. This user-friendly calculator allows you to visualize and configure file access levels effortlessly, translating intricate octal notations into an intuitive format.
The Umask Calculator assists in determining the default file permissions for newly created files and directories, making it easier to manage access from the start. Together, these tools provide a comprehensive solution for mastering file security in Linux.
Table of Contents
Procedure to check file permissions in Linux
- Open the terminal application.
- Type ls -l command
- Press Enter to run the command.
- This will give you a list of all the files in the current directory, along with their permissions.
This article is part of the following series.
- A Beginner’s Guide to Linux File Permissions
- 2 ways to check file permissions in Linux
- 2 ways to change file permissions in Linux
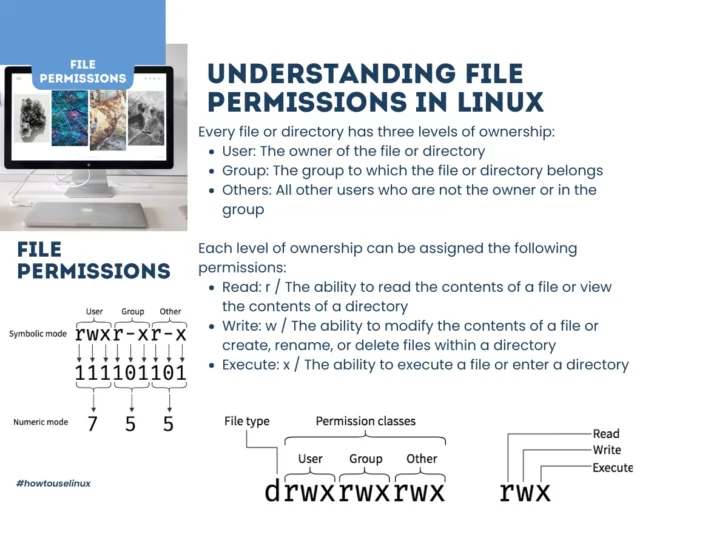
Understanding file permissions in Linux
Every file or directory has three levels of ownership:
- User owner (u).
- Group owner (g).
- Others (o).
Let’s see the details.
- Level: Description
- User: The owner of the file or directory
- Group: The group to which the file or directory belongs
- Others: All other users who are not the owner or in the group
Each level of ownership can be assigned the following permissions:
- Read (r).
- Write (w).
- Execute (x).
- Permission: Symbol / Description
- Read: r / The ability to read the contents of a file or view the contents of a directory
- Write: w / The ability to modify the contents of a file or create, rename, or delete files within a directory
- Execute: x / The ability to execute a file or enter a directory
Let’s see an example.
rw-r--r--
In this example, the owner of the file test.txt has access to “Read and write”, while other members of its group, as well as all other users, have “Read-only” access. Therefore, they can only open the file, but cannot make any modifications.
- User: rw-
- Description: The owner of the file has read and write permissions but cannot execute the file.
- Group: r–
- Description: Users in the file’s group have read permission but cannot write or execute the file.
- Others: r–
- Description: All other users have read permission but cannot write or execute the file.
This is called Symbolic mode. This mode is used to set permissions for a file or directory using a combination of letters and symbols.
To learn more about file permissions, I would highly recommend the following guide.
Understanding numeric mode of file permissions in Linux
There is another mode of file permissions: numeric mode.
Every file or directory on a Linux system has its own set of permissions and each permission can represented by a number.
The most common numerical representation is 3-digit notation for example 744. It consists of three numbers between 0 – 7 that represent user, group, and other respectively.
Lets see an example.
In the permission value 744, the first digit corresponds to the user, the second digit to the group, and the third digit to others. The first number is 7 then it indicates read write and execute access are granted to the owner of file.
It looks like this:
- Level: Permission / Binary / Decimal
- Owner: rwx / 111 / 7
- Group: r– / 100 / 4
- Others: r– / 100 / 4
In this example, the owner of the file has read, write, and execute permissions (represented as rwx), which is equivalent to the binary value 111 and the decimal value 7.
The group and others only have read permission (represented as r–), which is equivalent to the binary value 100 and the decimal value 4.
Here’s a list of the octal values for different file permissions:
- Decimal: Binary / Symbolic
- 0: 000 / —
- 1: 001 / –x
- 2: 010 / -w-
- 3: 011 / -wx
- 4: 100 / r–
- 5: 101 / r-x
- 6: 110 / rw-
- 7: 111 / rwx
Let’s see another example.
So, if you wanted to set the owner to have read, write, and execute permissions (rwx), the group to have read and execute permissions (r-x), and others to have no permissions (—), you can use an octal value of 740
File permission examples in Linux
Here are more commonly used file permission examples.
Some file permission examples:
- Permission: Owner / Group / Others
- 777: rwx / rwx / rwx
- 755: rwx / r-x / r-x
- 644: rw- / r– / r–
Some directory permission examples:
- Permission: Owner / Group / Others
- 777: rwx / rwx / rwx
- 755: rwx / r-x / r-x
Check file permissions with ls command in Linux
The ls -l command is a more efficient way to check file permissions in Linux. It specifically displays file permissions in a detailed format along with other information such as file size, last modification date, owner, group, and file name.
To use this method, simply type “ls -l filename”. Replace “filename” with the name of the file or folder you are looking for.
Let’s say if I want to find the permission of a file called “testfile”, I will type “ls -l testfile”. From the following example, the permission of testfile is rw-r–r–.
% ls -l testfile
-rw-r--r-- 1 howtouselinux staff 0 3 3 21:04 testfile
- File type: –
- Permission settings: rw-r–r–
- User owner: howtouselinux
- Group owner: staff
The first dash indicates that this is a regular file, and not a directory. The next three characters (rw-) indicate the owner’s permissions– in this case, the owner can read and write to the file, but cannot execute it.
The next three characters (r–) indicate the group permissions– in this case, members of the group can only read the file, and cannot write to or execute it.
The last three characters (r–) indicate the other permissions– anyone can only read the file, and cannot write to or execute it.
Find file Permissions with stat command in Linux
The “stat” command is another Linux command that can be used to get file permissions. To use “stat”, simply type “stat filename” at the command prompt. This will give you a detailed output of all the permissions for the file.
For example, the output of “stat test.txt” looks like this:
File: ‘test.txt’
Size: 0 Blocks: 0 IO Block: 4096 regular empty file
Device: fd01h/64769d Inode: 262094 Links: I-Node
uid=1001(user) gid=1001(user) mode=0644(rw-r--r--)
- File name: test.txt
- Size: 0
- Blocks: 0
- IO Block: 4096
- File type: Regular empty file
- Device: fd01h/64769d
- Inode number: 262094
- Links: I-Node
- User ID: 1001 (user)
- Group ID: 1001 (user)
- Permission settings: 0644 (rw-r–r–)
The first line shows the name of the file, its size, and what type of file it is. The next line shows the device number and inode number. The inode number is a unique number that identifies each file on a Linux system.
The third line shows the owner’s permissions, group permissions, and other permissions.
In this case, the file permission is 644( rw-r–r–). The owner can read and write to the file, members of the group can read the file, and anyone can read the file.
Change file permissions in Linux
Now that we know how to check file permissions. Let’s see how to change them with chmod command.
The “chmod” command stands for “change mode”. To use “chmod”, simply type “chmod +x filename” to give the file executable permissions, or “chmod u+w filename” to give the owner write permissions.
You can also use “chmod -x filename” to remove executable permissions, or “chmod u-w filename” to remove write permissions.
- Command:
chmod 700 file.txt- Description: Set permissions to read/write/execute for the owner, and no permissions for others.
- Command:
chmod 755 file.txt- Description: Set permissions to read/write/execute for the owner, and read/execute for others.
- Command:
chmod 644 file.txt- Description: Set permissions to read/write for the owner, and read-only for others.
- Command:
chmod +x file.txt- Description: Add execute permission for the owner, group, and others.
- Command:
chmod u+rw,g-w,o-rwx file.txt- Description: Add read/write for the owner, remove write for the group, and remove all permissions for others.
- Command:
chmod -R 700 dir- Description: Set permissions to read/write/execute for the owner and no permissions for others recursively for the directory ‘dir’.
Case study: file permissions for SSH private key file
Some files in Linux have special files permissions. I will use SSH private key as an example below.
An SSH private key is an encryption key used for secure communication between a client and a server.
It is a part of the SSH (Secure Shell) protocol and is used to establish secure connections over an insecure network, such as the Internet.
The private key is kept on the client machine and is used to decrypt the data that is encrypted with the corresponding public key on the server.
If the private key file has too permissive permissions, it can be read by unauthorized users.
This would allow them to use the private key to gain access to the server, potentially compromising sensitive information.
As we can see that this is a very important file. Allowing others to read the contents of the file can be a security risk.
The permissions for a private SSH key file should be set to 600 (read/write for the owner, no permissions for others).
This ensures that only the owner of the key file can read its contents and use it for authentication.
Case study: Permission denied error in Linux
Permission denied error is a common issue I met before. This can happen for a variety of reasons, but the most common cause is that the user does not have the necessary privileges to complete an operation.
I was confused when I got this error at first time because I had always been able to access that directory without any issues.
After the cross checking, I realized that the problem was with the permissions of the directory.
I used the ls -l command to check the permissions of the directory and noticed that the x permission was not set for some reason. The x permission allows a user to enter a directory.
Then I switched to root account and used the chmod command to add the x permission.
chmod +x directory_name
Problem solved.
So in order to resolve a permission denied error, the user must acquire the necessary privileges from their system administrator or root user.
Conclusion
In this blog post, I discussed two ways to check file permission in Linux- using the ls command and using the stat command. I also discussed what each of the ls output means and how you can change file permissions.
I hope you will find this guide helpful. If you face any issue while command execution or want to suggest what should I cover next, let me know in the comments.

Manny Heri
Saturday 27th of July 2024
Excellent overview of managing file permissions in Linux! Understanding permissions is fundamental to system administration and security. I particularly appreciate the breakdown of the ls -l command output, which is a quick way to grasp the permissions at a glance.
For those who might be new to Linux, it's worth noting that permissions are not just about readability or writability; they also define who can execute a file, which is crucial for security. I'd also recommend getting familiar with the chmod command for changing permissions and setfacl for more granular control with Access Control Lists (ACLs).
One tip I've found useful is to use symbolic modes in chmod for clarity, like chmod u+x file.txt to give the user execute permission. Also, remember that directory permissions affect the ability to access files within them, not just the directories themselves.
Another point to consider is the use of umask to set default permissions for newly created files and directories. This can be a great way to enforce a certain level of permission restrictions system-wide.
Thanks for the informative article! It's a solid starting point for anyone looking to tighten up their Linux file security. Looking forward to more in-depth discussions on file and directory management.
David Cao
Saturday 27th of July 2024
Thanks a lot for the comment.
Lucy
Thursday 16th of November 2023
Cool. It covers everything for file permissions in Linux.